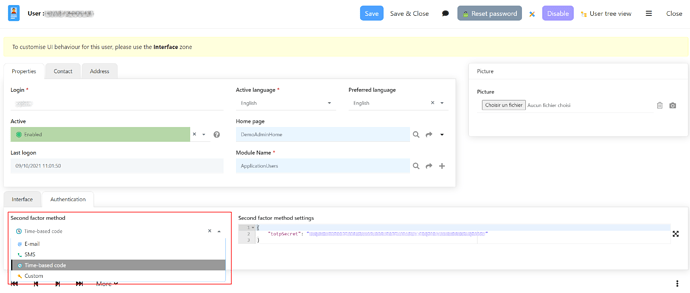
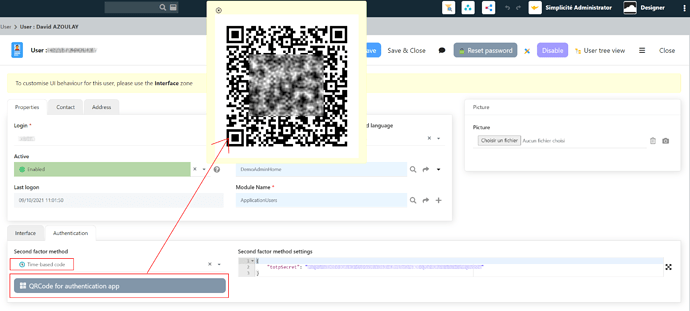
As of version 5.1 (starting with revision 5.1.1) an basic MFA (multi factors authentication) will be available on the internal UI authentication.
Warning : As it is still an experimental feature, the principles decribed bellow may change in the future.
A new yes/no system parameter can be overriden (either globally or on a per-user basis): USE_MFA to enable a second factor authentication.
This second factor is an OTP (one time password) mechanism.
By default, the OTP (a 6 digits number) is sent by by email, so it will only work if the users have an email address and, of course, if the mail service is will configured on your instance.
As of - not yet released - revision 5.1.2, it will be possible to override/extend it by implementing 2 new platform hooks: initMFA and checkMFA.
E.g. to use a first 4 digit OTP sent by SMS (with a fallback to default mechanism above), the implementation of these hooks can be something like:
@Override
public boolean initMFA(HttpServletRequest request, HttpServletResponse response) throws Exception {
HttpSession session = request.getSession();
Grant g = ServletTool.getGrant(session);
try {
String otp = Tool.randomNumber(4); // Generate a 4 digits OTP code
session.setAttribute(MFA_OTP, otp); // Store it in the session
AppLog.info("OTP for user " + g.getLogin() + " = " + otp, g);
String num = g.getMobilePhoneNumber();
if (Tool.isEmpty(num))
throw new Exception("User " + g.getLogin() + " has no mobile phone number"); // SMS can only be sent to a mobile phone number
if (SMSTool.sendSMS(g, num, "Your one time code is " + otp) == null) // null means SMS_SERVICE is not well configured or that an issue occured on the SMS service provider side
throw new Exception("Error sending SMS");
return true;
} catch (Exception e) {
AppLog.warning(null, e, g);
return super.initMFA(request, response); // Fallback to default MFA (= email)
}
}
In this case the check method (comparing the entered value with the one stored in the session) is the same as the default so the checkMFA hook does not need to be implemented.
Note that this obviously also require a SMS service provider to be well configured on your instance.
In a future revision a third party TOTP Java lib will be included allowing TOTP-based custom MFA implementations, this will be described later… stay tuned…